To
configure packet capture on a PAN Firewall, go to Monitor > Packet Capture
> click Manage Filters (hyperlink).
Click Add.
Under Id column > select: 1.
Under Ingress Interface column > select ethernet1/2 (inside Security Zone).
Under Source column > type Source: 192.168.1.20 (inside client machine) > type Destination: 192.168.50.10 (DMZ machine) > under Proto > type 1 (ICMP).
Notice the Filters Set incremented to 1 (1/4). Click toggle for Filtering to set it ON.
Under Configure Packet > Stage > Add > select Stage: receive (receive from the PAN Firewall's perspective).
Click on Packet Capture (OFF) to toggle to ON and start the Packet Capture.
A Packet Capture Warning message is displayed. Click OK to continue.
I tried pinging from a inside client machine (192.168.1.20) to DMZ server (192.168.50.10).
Click on any packet capture sequence number > expand Internet Protocol version 4 (Layer 3 info) > notice under Flags > ICMP (1)
It's best practice to remove all Packet Capture filters on the PAN Firewall afterwards. Click Clear All Settings under Settings.
The Capture Files will still be retained. Just click on the selected Captured File > Delete (at the bottom) to manually remove them.
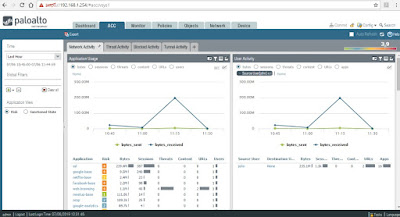
Under Network Activity tab > you can view Application Usage graphs (widget on the left): bytes, sessions, threats, content, URLs or users.
You can change the type of graph on the widget's upper right corner (click line).
You can view more details by selecting a specific Application (facebook-base) > Value.
You can also filter to display a specific Application by just clicking on the selected Application (netflix-base).
Just click on the "x" mark beside the Application to remove the Global Filter.
This is Application Usage view by sessions.
This is Application Usage view by threats.
This is Application Usage view by content.
This is for Application Usage view by URLs.
This is for Application Usage view by users.
This is Threat Activity tab.
This is Blocked Activity tab.
This is Tunnel Activity tab.
You can also filter on a specific user under User Activity (widget on the left) > hover to the user > Add Global Filter.
This is User Activity > Source User (john) > bytes.
This is User Activity > Source User (john) > sessions.
This is User Activity > Source User (john) > threats.
This is User Activity > Source User (john) > content.
This is User Activity > Source User (john) > URLs.
This is User Activity > Source User (john) > apps.
You can also combine User Activity view on a Source User (john) and an Application Usage (facebook-base). Hover on facebook-base > Add Global Filter.
You can also export the graphs into a report. Just click Export which is the PDF icon above Network Activity tab.
Ensure pop-up blocker on the web browser is allowed for the PAN Firewall. In Google Chrome web browser, just click on square with red mark (on the rightmost corder beside the star/Favorite icon) > Always allow pop-ups from https://192.168.1.254 > Done.
The PDF report is downloaded (at the bottom) on the client machine after pop-ups was allowed.
This report can be shared to management or a non-technical person, i.e. Sales.
Click Add.
Under Id column > select: 1.
Under Ingress Interface column > select ethernet1/2 (inside Security Zone).
Under Source column > type Source: 192.168.1.20 (inside client machine) > type Destination: 192.168.50.10 (DMZ machine) > under Proto > type 1 (ICMP).
Notice the Filters Set incremented to 1 (1/4). Click toggle for Filtering to set it ON.
Under Configure Packet > Stage > Add > select Stage: receive (receive from the PAN Firewall's perspective).
Type a
name for the File (ICMP-PCAP-1) > type Packet Count: 100 > type Byte
Count > 1000 > click OK.
The Packet Capture will automatically stop if it either hits a Packet
Count of 100 first or it reached a Byte Count of 1000 bytes. It's recommended to keep
the Packet Capture file as small as possible to avoid overwhelming the PAN Firewall's CPU and memory.
Click on Packet Capture (OFF) to toggle to ON and start the Packet Capture.
A Packet Capture Warning message is displayed. Click OK to continue.
I tried pinging from a inside client machine (192.168.1.20) to DMZ server (192.168.50.10).
The
Packet Capture file will show on the left hand side under Capture Files. Just
click Refresh (beside Help) if there's still no output.
Click on
the Captured File (ICMP-PCAP-1) to download the pcap file. You'll need a Wireshark network protocol analyzer in order to open a packet capture (.pcap) file.
Click on any packet capture sequence number > expand Internet Protocol version 4 (Layer 3 info) > notice under Flags > ICMP (1)
It's best practice to remove all Packet Capture filters on the PAN Firewall afterwards. Click Clear All Settings under Settings.
The Capture Files will still be retained. Just click on the selected Captured File > Delete (at the bottom) to manually remove them.
You can
view top users and application using the PAN Firewall Application Command
Center (ACC) under ACC tab.
You can
view graphs by Time: Last 15 Minutes, Last Hour, Last 6 hours, etc.
Under Network Activity tab > you can view Application Usage graphs (widget on the left): bytes, sessions, threats, content, URLs or users.
You can change the type of graph on the widget's upper right corner (click line).
You can view more details by selecting a specific Application (facebook-base) > Value.
You can also filter to display a specific Application by just clicking on the selected Application (netflix-base).
Just click on the "x" mark beside the Application to remove the Global Filter.
This is Application Usage view by sessions.
This is Application Usage view by threats.
This is Application Usage view by content.
This is for Application Usage view by URLs.
This is for Application Usage view by users.
This is Threat Activity tab.
This is Blocked Activity tab.
This is Tunnel Activity tab.
You can also filter on a specific user under User Activity (widget on the left) > hover to the user > Add Global Filter.
This is User Activity > Source User (john) > bytes.
This is User Activity > Source User (john) > sessions.
This is User Activity > Source User (john) > threats.
This is User Activity > Source User (john) > content.
This is User Activity > Source User (john) > URLs.
This is User Activity > Source User (john) > apps.
You can also combine User Activity view on a Source User (john) and an Application Usage (facebook-base). Hover on facebook-base > Add Global Filter.
You can also export the graphs into a report. Just click Export which is the PDF icon above Network Activity tab.
Ensure pop-up blocker on the web browser is allowed for the PAN Firewall. In Google Chrome web browser, just click on square with red mark (on the rightmost corder beside the star/Favorite icon) > Always allow pop-ups from https://192.168.1.254 > Done.
The PDF report is downloaded (at the bottom) on the client machine after pop-ups was allowed.
This report can be shared to management or a non-technical person, i.e. Sales.














































No comments:
Post a Comment